Big Tech steals your data
- dhruvtalksstech
- Feb 8, 2023
- 6 min read
Updated: Feb 21, 2023
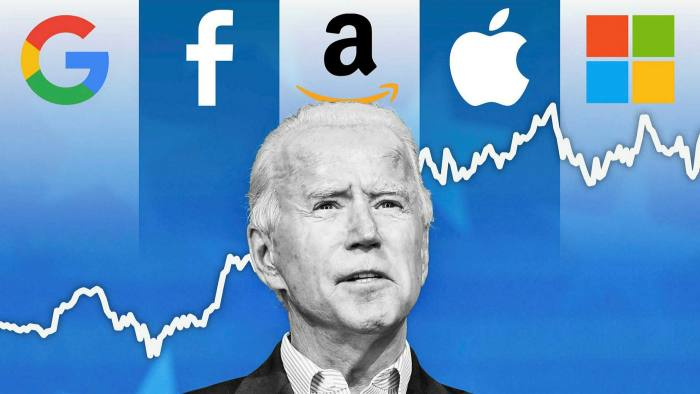
Big Tech is notoriously known for stealing the data of its users. I believe that social media is such as integral part of our lives that I am not able to discourage its usage even among my users who have a very staunch stance against it. That is why I think we need to learn to co-exist with it. Social media is gaining increasing relevance in today's world. On the flip side, we are all victims of cross-app tracking and privacy infringement. Since one cannot deny the industry's exponential growth, it only makes sense to create a social media tool that retains all the functionality while preventing spying, data brokering, and misuse of personal information. One way to achieve that is by designing apps centered around consent and eliminating the use of cookies embedded in social media apps. The recent Nobel laureates for Physics have also opened doors to Quantum computing which can help social media apps become safer through quantum encryption and using the entanglement concept to enable secure communications without crunching exabytes of data.



It would also make it difficult for hackers to observe data in transit without breaking the chain or leaving a footprint. It is a well-known fact that social media companies sell data to brokers. Instead of engaging in such underhanded money-making, social media companies and the fast-growing app industry should rely more on subscriptions and sponsorships to sustain the business -- taking the organic route. Social media apps should be online spaces where friends and family interact freely and securely. Privacy infringement, data brokering, and user tracking plague our tech-driven society. Advertisers track our every move, create a digital identity of us without our consent, and accumulate data throughout our life.



Our most intimate pictures and texts are visible to a data analyst simply because systems have no end-to-end encryption. For far too long, we have unwittingly fed our data in the interest of unfair data collection, mapping, recognition, and tracking. Once I embarked on this journey of technology consciousness, it became a daily practice for me to stay updated and scrutinize privacy and security details. Social media has gained immense control of our lives, and they hold the power to sway our personal decisions and even elections. Even the Wall Street Journal concluded that Facebook fueled riots in India and led to genocide in Myanmar. I receive many emails daily telling me how my privacy tips helped curb a hacking attempt. I also started to give pro-privacy and tech tips at the end of my blogs at one point for a brief time. I think I should start that again. What do you guys think?



If a few hundred thousand views can do so much, imagine what 2 billion iPhone and 3.5 billion Android users employing simple but vital steps, like eliminating cookies from browsers and increasing checks on apps uploaded to Play Store, can do. I want to bring all these tech safety measures to the forefront of discussions and be heard in the world's highest offices.
Technology is growing at an unprecedented pace but so are imposters who wish to misuse this technology. So, we need to be careful with how we design technology. Computer Science - ironically the field that made all digital advancement possible but not without creating a few monsters along the way - also holds the answer to all of this. I developed an Image Recognizer App through the technologies I had learned.



I prioritized privacy and security over functionality and data collection. I ensured that the photos the users took were not saved on any server. The app does not go through the files and media on the user's device or save the images taken to the gallery. It does not employ cross-app tracking or learn user habits, which is why the app does not serve ads in any way. My tech blog revolving around privacy and security issues received appreciation from readers worldwide, acting as a driving force for me. I have educated myself on how technology works and how we can stay safe in the modern age where the adoption of free platforms proliferates rapidly. For far too long, we have unwittingly fed our data in the interest of unfair data collection, mapping, recognition, and tracking.



Technology is growing at an unprecedented pace but so are imposters who misuse this technology. So, we need to be careful with how we design technology. I am passionate about advocating the cause of cybersecurity for individuals and organizations. I aim to strengthen the field of data protection in my years as a blogger. In the context of my account hacking, after my Google account was hacked in December, it haunted me for a long time. For weeks, I spent hours sobbing in corners of the house where no one could see me. With each threat from the hacker, my situation worsened. There were even times when I thought of physically harming myself.



The hacker had left a deep mark on me. I always felt I was being watched and was scared even to use my phone and laptop, fearing someone was keeping tabs on everything I was doing. I wish to develop a high-level sensitivity logic for tracking differential privacy.



I am excited to develop next-gen anonymous and censorship-resistant communication and design systems. operations would be end-to-end encrypted, utilize decentralized monitoring systems, and use quantum encryption and entanglement to secure communications and data without crunching terabytes of data. Thus, ensuring that it is impossible for hackers to observe data in transit without breaking the chain or leaving a footprint. There need to be companies that use AI to solve the problem of false information entered by users to bypass content restrictions while ensuring that the data is not stored anywhere or manipulated by governments for political propaganda. Further, by formulating an industry standard, businesses should provide private relaying and encrypting services to Android and iOS users across platforms like Google, Instagram, and Twitter.



To enforce data privacy, they should also set up services to allow users to directly view, modify and delete the data stored in data centers. Although Big Tech claims that they do not go over our data, there is no way for the commoner to know what portion of their data is being stored and analyzed by the companies’ data scientists. Thus, ways social media apps can generate revenue without relying heavily on ads that require tracking user habits and behaviors should be innovated.


The purpose of a business is to make a profit, and that is where the effort to generate revenue through subscriptions and sponsorships would come into play. Data collected for advertising should be restricted to analyzing generic data preferences over sensitive personal data. The organizations would also optimize sites to work sans cookies while still being able to analyze analytics about the site’s performance. Still, the key is to ensure that the data is presented in a raw form without personal details such as exact neighborhood, device name, and browser type. Eventually, I wish this technology is a must for all electronic devices to ensure that we can still connect with the world without jeopardizing our personal lives. Our digital lives should bring people together and not fuel riots, influence elections, and cause genocides.



If I had to define today's scenario in a couple of sentences, I would say - Tweeting from the Data Centers: How Big Tech siphons and manipulates data, invade our privacy, swings elections, and influences our decisions and the immense control eccentric tech billionaires have over our personal life and data. I think I should invite Mark Weinstein, founder of MeWe – a visionary social media site, and a renowned data privacy expert, to come to talk about privacy on my blog. He would educate us about data security and privacy. I am interested to know what you guys think about privacy, social media, and Big Tech. They are extremely powerful, and influential and it is we who have allowed them to control every little aspect of our personal lives.


SUBSCRIBE TO MY FORMS AND YOU WILL BE THE FIRST TO KNOW WHEN A BLOG GOES UP AND LIVE
If you made it this far, a sub to my updates would be ………. BIG !!!!!
JAI HIND
JAI BHARAT
VANDE MATRAM

THE EVILEST PEOPLE ON THE PLANET



Real-life oxymoron




Comments